The Examination Pattern
When examiners evaluate ICFR logical access controls, they don't start with firewalls or encryption. They start with identity.
- "Show me who can approve journal entries in your general ledger."
- "Show me how you granted that access."
- "Show me when you last reviewed whether that access is still appropriate."
If you can't answer these questions with confidence (and attributable evidence) — you fail. Not because your security tools are inadequate, but because your identity governance is ungoverned.
The common failure pattern:
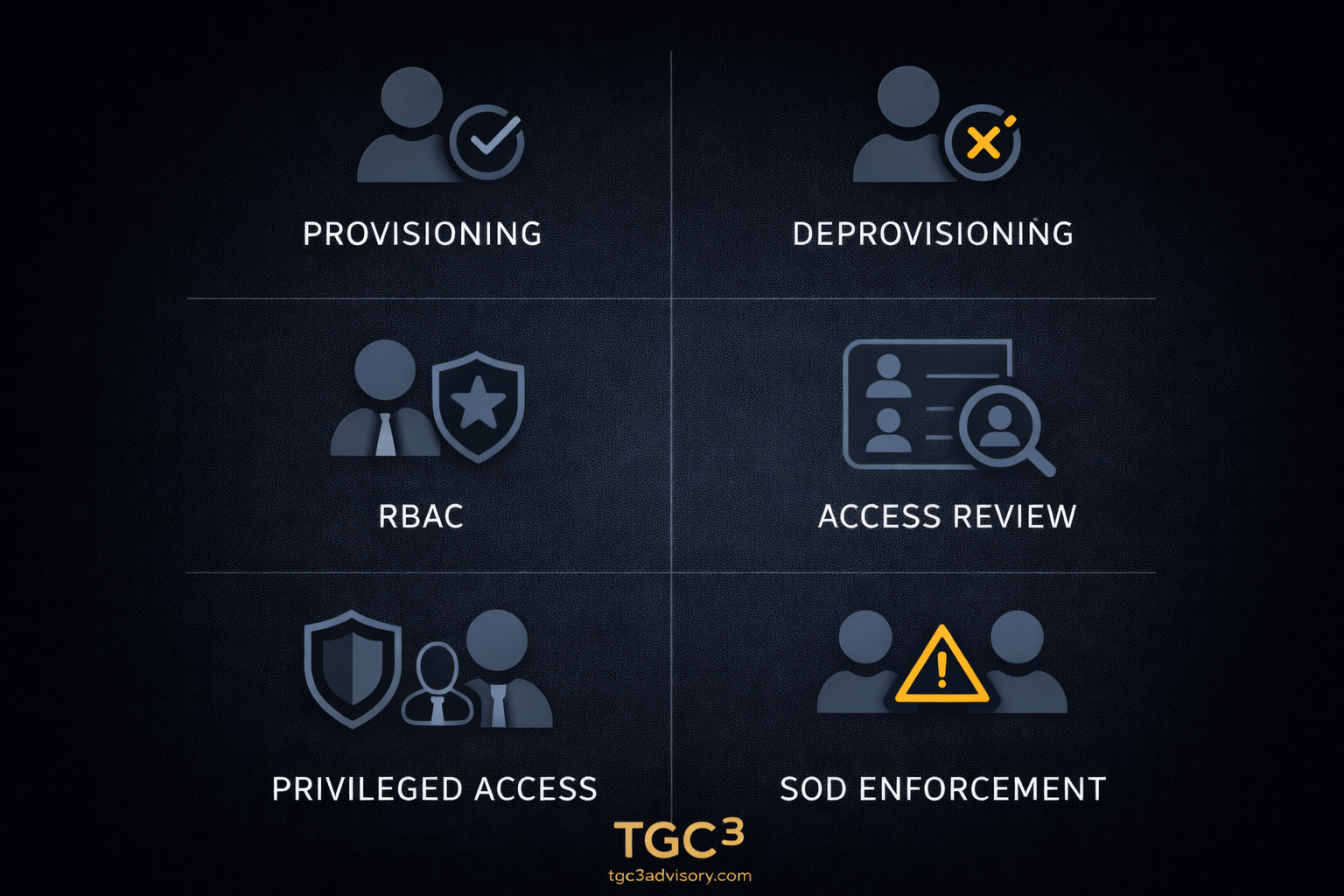
- Access granted via email request (no formal approval record)
- Roles assigned inconsistently (no authoritative role model)
- Access reviews performed in spreadsheets (no retained evidence)
- Segregation of duties conflicts identified manually (no systematic enforcement)
- Deprovisioning triggered by informal notification (no integration with HR systems)
These aren't security gaps. They're identity governance gaps.
Why Identity Is the Control Plane
Every material ICFR control depends on access decisions:
- Segregation of duties controls require you to know who has conflicting access and prevent those conflicts at provisioning
- Change management controls require you to know who can modify production systems and enforce approval workflows
- Transaction authorization controls require you to know who can initiate vs. approve financial transactions
- Data integrity controls require you to know who can create, modify, or delete financial records
You cannot enforce any of these controls if you cannot govern who has access.
Identity governance isn't a subdomain of cybersecurity. It's the foundational architecture that makes financial controls defensible.
1. Provisioning Governance
- Formal access request with documented business justification
- Manager approval with segregation of duties pre-validation
- Role-based access assignment mapped to job function
- Evidence: request record, approval timestamp, role assignment log
2. Deprovisioning Governance
- Termination-triggered access removal (same business day)
- Transfer-triggered access review and role reassignment
- Retention policies for disabled accounts
- Evidence: HR event linkage, deprovisioning timestamp, audit trail
3. Role-Based Access Control (RBAC) Design
- Roles mapped to job functions and segregation of duties requirements
- Role-to-entitlement mappings maintained and reviewed
- Role assignments drive provisioning (not ad-hoc entitlements)
- Evidence: role library, role-to-risk mapping, assignment records
4. Access Review Governance
- Quarterly manager attestation with role and entitlement visibility
- Exception workflows for access that doesn't match expectations
- Dormant account identification and automated disablement
- Evidence: signed attestations, identified conflicts, remediation tracking
5. Privileged Access Governance
- Separate administrative accounts for elevated privileges
- Executive approval for privileged access assignments
- Just-in-time access provisioning for temporary admin needs
- Privileged session logging and monitoring
- Evidence: privileged user inventory, approval records, session logs
6. Segregation of Duties Enforcement
- SoD conflict matrix mapped to financial process risks
- Automated conflict detection during provisioning
- Compensating controls for unavoidable conflicts
- Evidence: conflict matrix, detection logs, risk acceptance records
Why do most financial institutions or banks fail?
The pattern we see repeatedly: institutions implement IAM tools but never design the governance mechanisms that make those tools defensible.
Common failure modes:
"We have SailPoint, so we're compliant."
Having an IAM platform doesn't mean you have identity governance. If your role model is incomplete, your access reviews are performative, and your provisioning workflows bypass systematic approval — the tool is irrelevant.
"We review access quarterly."
Examiners don't accept "we review access." They want to see: Who reviewed what? What criteria triggered the review? What conflicts were identified? What remediation occurred? If your evidence is an email someone sent or a spreadsheet someone signed — you have documentation, not governance.
"We enforce segregation of duties."
How? Do you have a documented SoD conflict matrix? Is it enforced at provisioning or detected after the fact? Are conflicts automatically prevented or manually identified? If the answer is "we're working on that" — you don't enforce segregation of duties.
"HR tells us when people leave."
Via what mechanism? Email notification when someone remembers? Ticket submission with variable SLAs? Integration between HR systems and IAM platforms with automated triggers? If the answer is anything other than systematic, automated, same-day deprovisioning — you have a material control weakness.
What Does Defensible Identity Governance Look Like?
When examiners ask:
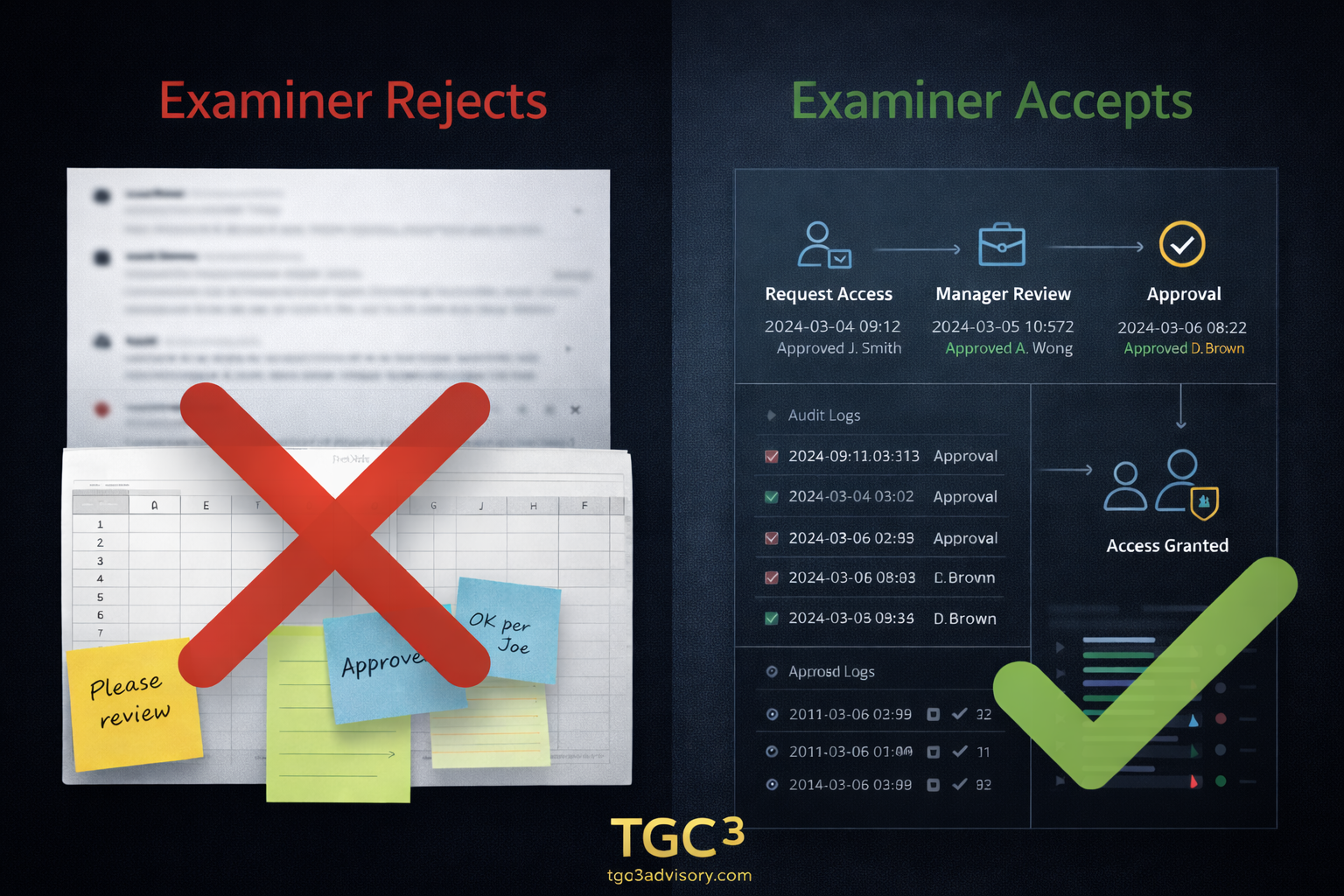
"How do you grant access to financial systems?"→ Formal request submitted through provisioning workflow. Manager approves with documented business justification. System validates no segregation of duties conflicts. Role assigned based on job function. Access granted. All steps timestamped and retained.
"How do you know privileged access is appropriate?"→ Privileged user inventory maintained. Quarterly recertification with IT Director or CFO sign-off. Business justification documented for each privileged assignment. Just-in-time access used for temporary admin needs. Privileged sessions logged and monitored. All evidence retained.
"What happens when someone is terminated?"→ HR system triggers deprovisioning workflow automatically. Access disabled same business day across all systems. Disabled account retained for 90 days then deleted. Audit trail maintained. No manual notification required.
"How do you enforce segregation of duties?"→ SoD conflict matrix documented and approved by Risk Committee. Conflicts automatically detected during provisioning. System prevents conflicting role assignments. Compensating controls documented for approved exceptions. Quarterly conflict reviews identify drift. Evidence: conflict matrix, detection logs, exception approvals, review attestations.
Not policies describing these processes.
Evidence proving they operated.
The First Step
Identity governance is not a multi-year transformation. It's a systematic design problem with a clear remediation path.
The institutions that pass ICFR examinations aren't the ones with the most sophisticated tools. They're the ones with clear provisioning mechanisms, documented role models, formal access reviews, defensible privileged access governance, and systematic segregation of duties enforcement.
Start with assessment: Can you answer examiner questions with evidence today? If not, what mechanisms are missing?
Then design the governance spine that makes identity defensible.
Not sure whether your identity governance can withstand examination? Our 9-Domain ITGC Assessment diagnoses control design, operational effectiveness, and evidence quality — then delivers a remediation roadmap to baseline exam readiness.